Comprehensive Cybersecurity Solutions: From Network Monitoring to Advanced Threat Detection and Response
Comprehensive Managed SIEM Service for Businesses
A managed SIEM service offers a comprehensive approach to security information and event management. By outsourcing your managed SIEM service, businesses can monitor, detect, and respond to security threats in real time. It ensures 24/7 visibility into network activity, protecting against potential cyber threats while alleviating the burden on in-house IT teams.
Enhance Security with CrowdStrike Falcon LogScale Integration
The CrowdStrike Falcon LogScale Integration provides a powerful combination of threat detection and log analysis capabilities. With CrowdStrike Falcon LogScale Integration, organizations benefit from real-time security insights, improved scalability, and enhanced efficiency in detecting and mitigating threats across their network infrastructure, ensuring optimal protection against cyber attacks.
Top Managed SIEM Providers for Advanced Cybersecurity
Managed SIEM providers deliver advanced security monitoring and threat detection services to businesses of all sizes. By working with managed SIEM providers, organizations can streamline their security operations, reduce the risk of data breaches, and ensure that their IT environments are continuously monitored by experienced cybersecurity professionals.
Optimize Cybersecurity with Managed XDR Service
A managed XDR service extends traditional detection and response capabilities by providing comprehensive security across multiple environments. With a managed XDR service, businesses can detect and respond to advanced threats faster, utilizing automated responses and threat intelligence to ensure comprehensive protection across networks, endpoints, and cloud services.

Streamlined Threat Detection via LogScale Integration
The CrowdStrike LogScale Integration enhances an organization’s ability to collect and analyze large amounts of security data efficiently. By using CrowdStrike LogScale Integration, companies can scale their logging infrastructure while improving the accuracy and speed of threat detection, allowing faster responses to potential security incidents.
Secure and Scalable Logging with LogScale CrowdStrike
LogScale CrowdStrike offers an efficient logging solution that enhances real-time threat detection and response. By implementing LogScale CrowdStrike, businesses gain better visibility into their networks, allowing them to identify security incidents quicker, improve data retention, and scale security operations seamlessly.
Leading SOC Providers for 24/7 Cybersecurity Monitoring
Leading SOC providers offer outsourced security operations services that provide 24/7 monitoring, threat detection, and response. Working with SOC providers ensures that businesses can access expert security services without the need to build and maintain an in-house security operations center, saving time and resources.
Improve Threat Detection Using CrowdStrike LogScale
CrowdStrike LogScale offers businesses a powerful tool for managing and scaling their log data, enabling faster threat detection and resolution. With CrowdStrike LogScale, companies can improve their visibility into network activity, enhance their cybersecurity posture, and streamline their threat response efforts.

Trusted Cyber Security Monitoring Companies for Protection
Top cyber security monitoring companies help businesses protect their digital assets through continuous monitoring and advanced threat detection. By partnering with cyber security monitoring companies, organizations can stay ahead of potential threats, ensuring that they maintain strong defenses against evolving cyber attacks.
Strengthen Cybersecurity with Cisco SIEM Solution
The Cisco SIEM solution provides businesses with real-time monitoring and analysis of security events across their network. Using the Cisco SIEM solution, companies can enhance their security visibility, identify potential threats faster, and ensure compliance with industry regulations, all while reducing the complexity of managing security operations.
CrowdStrike EDR Solution for Enhanced Endpoint Security
The CrowdStrike EDR solution offers advanced endpoint detection and response capabilities, allowing businesses to detect and respond to security threats in real time. With the CrowdStrike EDR solution, organizations can protect their endpoints from malware, ransomware, and other sophisticated attacks while ensuring rapid incident response.
Advanced Log Management with Falcon LogScale Technology
Falcon LogScale is a key component of CrowdStrike’s advanced cybersecurity platform, providing enhanced log management and threat detection capabilities. By leveraging Falcon LogScale, organizations can scale their logging infrastructure efficiently while improving the accuracy and speed of their security operations.
Real-Time Threat Detection with Reliable SIEM Service
A SIEM service provides businesses with a centralized platform for monitoring and analyzing security events across their network. By using a SIEM service, organizations can improve their ability to detect and respond to potential threats while reducing the time and resources required to manage security operations.
Cost-Effective Security with Outsourced SOC Services
An outsourced SOC allows businesses to benefit from expert security monitoring and incident response without the need to build and maintain an internal security operations center. With an outsourced SOC, companies can enhance their security posture while focusing on core business activities, ensuring comprehensive protection.
Expert Cybersecurity from Leading SOC Security Company
A SOC security company specializes in providing outsourced security operations services, including monitoring, threat detection, and incident response. Partnering with a SOC security company ensures businesses can protect their digital assets 24/7, without the need for costly in-house resources and infrastructure.
Comprehensive Protection with Falcon LogScale
Log management and real-time threat detection. With CrowdStrike Falcon LogScale, organizations can improve their ability to detect and mitigate security threats while reducing the time and effort required to manage their security operations.
SOC Managed Services for 24/7 Security Monitoring
SOC managed services provide businesses with a fully outsourced security operations center, offering 24/7 threat monitoring and incident response. By utilizing SOC managed services, organizations can benefit from expert security support without the need to invest in costly internal security infrastructure.
Secure Your Business with Outsourced SOC Services
Outsourced SOC services provide businesses with 24/7 monitoring and response capabilities, ensuring continuous protection against cyber threats. By leveraging outsourced SOC services, organizations can reduce the burden on internal teams, improve security efficiency, and access expert threat detection and response services.
Industry-Leading Protection from Best XDR Solutions
The best XDR solutions provide comprehensive, multi-layered threat detection and response capabilities across endpoints, networks, and cloud environments. By implementing the best XDR solutions, businesses can enhance their security posture, improve incident response times, and protect against sophisticated cyber attacks.
Boost MSP Network Security with Reliable Solutions
MSP network security solutions provide managed service providers with the tools and expertise to protect client networks from cyber threats. By offering MSP network security services, businesses can ensure that their clients’ networks remain secure while reducing the complexity and cost of managing network security in-house.
Advanced Threat Detection with Managed XDR Solutions
Managed XDR solutions offer businesses comprehensive detection and response capabilities across multiple security layers. By utilizing managed XDR solutions, organizations can detect and respond to sophisticated cyber threats in real-time, ensuring improved protection and minimizing the impact of security incidents.
Stay Secure with the Best XDR Solutions Available
The best XDR solutions provide businesses with end-to-end security across multiple environments, enabling faster threat detection and response. Implementing the best XDR solutions helps organizations enhance their cybersecurity posture, protect against advanced threats, and improve overall incident response effectiveness.
Trusted Managed SOC Service Provider for Protection
A managed SOC service provider delivers outsourced security operations services, including 24/7 monitoring and threat detection. By partnering with a managed SOC service provider, businesses can enhance their security operations, ensure compliance with industry standards, and protect their digital assets from evolving threats.
Enhance Cybersecurity with SIEM Security Services
SIEM security services offer businesses a centralized platform for managing and analyzing security events. By using SIEM security services, organizations can improve their threat detection capabilities, reduce the risk of data breaches, and streamline their security operations for better efficiency.
Fast Cyber Threat Remediation for Business Continuity
Cyber threat remediation involves identifying, mitigating, and resolving security threats that have affected a business. Effective cyber threat remediation ensures that organizations can recover from cyber attacks quickly, minimize damage, and prevent future incidents from impacting their operations.
Enhancing Cybersecurity with Network Security Monitoring Services
Network Security Monitoring Services are essential for keeping your business safe from cyber threats. These services provide real-time visibility into network traffic, enabling early detection of suspicious activities. By implementing Network Security Monitoring Services, organizations can identify and respond to security incidents before they cause significant damage. With advanced analytics and continuous monitoring, businesses can mitigate risks efficiently and maintain compliance with security regulations.
Exploring the Key Benefits of Cloud Computing Security
The Benefits of Cloud Computing Security are vast, offering scalable, flexible, and cost-effective protection for your digital assets. As businesses shift to the cloud, Benefits of Cloud Computing Security include enhanced data encryption, better compliance controls, and reduced risk of data breaches. Cloud security also supports robust access management, making it easier to control who can access sensitive information while maintaining seamless operations.
How XDR Solutions Improve Threat Detection and Response
XDR Solutions (Extended Detection and Response) are crucial for integrating multiple security tools and improving threat detection. With XDR Solutions, organizations can streamline incident response and increase visibility across endpoints, networks, and servers. This solution enables proactive identification of security gaps and delivers a coordinated defense, minimizing the impact of cyberattacks and accelerating recovery times.
Choosing the Right SIEM Provider for Your Business
Choosing a reliable SIEM Provider is critical for businesses aiming to manage and analyze security information efficiently. A top SIEM Provider offers robust tools that collect and aggregate data from various sources, providing deep insights into potential threats. By leveraging SIEM technology, companies can achieve real-time monitoring, enhanced compliance reporting, and improved incident response capabilities.

Effective Network Incident Response for Minimizing Cyber Risks
Network Incident Response is a structured process designed to address and manage security breaches swiftly and effectively. Through Network Incident Response, businesses can minimize downtime, reduce financial losses, and protect sensitive data. This service typically includes threat identification, containment, eradication, and recovery phases, ensuring a comprehensive approach to managing security incidents.
The Importance of Managed SOC Services for Continuous Security
Managed SOC Services offer businesses a dedicated team of cybersecurity experts who monitor and respond to security threats in real time. By utilizing Managed SOC Services, organizations can enhance their threat detection capabilities without needing to maintain an in-house team. This service ensures continuous network monitoring, swift incident response, and proactive threat hunting to keep businesses secure.
Leveraging MDR Security Services for Proactive Threat Detection
MDR Security Services provide businesses with advanced threat detection and response capabilities. By using MDR Security Services, organizations gain access to 24/7 monitoring and rapid incident response, ensuring that threats are identified and mitigated before causing harm. These services offer a cost-effective solution for businesses that want to improve their security posture without building an in-house team.
Comprehensive Threat Protection with XDR Service
XDR Service (Extended Detection and Response) is designed to extend security across multiple layers of an organization’s IT infrastructure. With XDR Service, businesses can detect and respond to advanced threats across endpoints, networks, and cloud environments. This holistic approach to threat detection reduces the time to detect and remediate security incidents, improving overall resilience.
Strengthening Cyber Defense with Managed XDR
A Managed XDR solution is an effective way for businesses to outsource their cybersecurity needs. By using Managed XDR, companies benefit from continuous monitoring and response to cyber threats across their IT infrastructure. This service integrates threat intelligence with machine learning to provide a comprehensive and proactive defense against evolving cyber threats.
Partnering with MDR Security Vendors for Optimal Cybersecurity
MDR Security Vendors play a vital role in helping organizations detect and respond to security threats. By partnering with MDR Security Vendors, businesses can enhance their threat detection capabilities and ensure rapid incident response. These vendors offer a range of managed services tailored to meet specific security needs, from monitoring to full incident management.
Streamlining Threat Monitoring with SIEM Management Services
SIEM Management Services ensure that your organization’s security information and event management systems are optimized and operating efficiently. Through SIEM Management Services, businesses can centralize security data, monitor threats in real-time, and streamline compliance reporting. This service allows organizations to focus on core operations while maintaining a strong security posture.
Ensuring 24/7 Protection with a Managed SOC Service
A Managed SOC Service provides businesses with around-the-clock security monitoring and incident response. With a Managed SOC Service, organizations can trust that experienced cybersecurity professionals are handling their security needs. This service ensures continuous threat detection, response, and remediation, allowing businesses to focus on growth while maintaining robust cybersecurity.
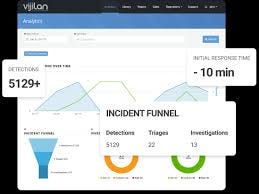
Combining SIEM Vendors and Advanced XDR Solutions for Superior Security
SIEM Vendors and Advanced XDR Solutions offer organizations cutting-edge tools to detect and mitigate cyber threats. Combining SIEM Vendors and Advanced XDR Solutions helps streamline the detection process, providing a holistic view of security events across an organization’s infrastructure. These services enable businesses to enhance their incident response while ensuring better threat visibility.
Improving Threat Visibility through XDR Cybersecurity Monitoring
XDR Cybersecurity Monitoring integrates various security layers to provide a unified defense against cyber threats. Through XDR Cybersecurity Monitoring, organizations can gain better visibility into their security landscape, making it easier to detect and respond to complex threats. This service helps reduce the time needed to identify potential attacks and strengthens an organization’s overall security.
Boosting Security Operations with Managed SIEM Services
Managed SIEM Services are designed to help businesses manage their security information and event management systems more effectively. With Managed SIEM Services, companies can enhance their security monitoring and gain deeper insights into potential threats. These services also ensure that businesses meet compliance requirements while focusing on strategic growth.
Understanding the Incident Handling Phases for Effective Response
The Incident Handling Phases are a set of structured steps for managing cybersecurity incidents. These Incident Handling Phases include identification, containment, eradication, recovery, and lessons learned. By following these phases, organizations can minimize the impact of security breaches and improve their future incident response capabilities.
Managed Extended Detection and Response for Comprehensive Cybersecurity
Managed Extended Detection and Response (MXDR) provides businesses with a comprehensive security solution that integrates detection and response across multiple attack vectors. With Managed Extended Detection and Response, organizations can ensure that threats are identified and mitigated before they cause significant damage, offering real-time protection and proactive defense.
The Role of Cybersecurity Remediation Services in Incident Recovery
Cybersecurity Remediation Services focus on identifying, mitigating, and resolving security incidents efficiently. With Cybersecurity Remediation Services, businesses can recover quickly from cyberattacks, reduce downtime, and prevent further damage. These services include patch management, system restoration, and vulnerability assessments to improve long-term security resilience.
Safeguarding Digital Assets with Continuous Cybersecurity Monitoring
Cybersecurity Monitoring is essential for businesses to detect potential threats and respond promptly. By implementing Cybersecurity Monitoring, organizations can safeguard their networks, endpoints, and data from evolving cyber threats. This service ensures continuous surveillance of digital environments, reducing the risk of breaches and enabling swift incident response.
Why MXDR Service Providers Are Critical for Modern Cybersecurity
MXDR Service Providers deliver comprehensive security solutions that encompass detection, response, and threat management. By partnering with MXDR Service Providers, businesses can enhance their cybersecurity posture without needing to manage internal teams. These providers offer continuous monitoring and expert response to threats across endpoints, networks, and cloud environments.
Navigating the Incident Response Phase for Swift Breach Recovery
The Incident Response Phase refers to the steps organizations take to manage and resolve security breaches. During the Incident Response Phase, teams work to identify, contain, and eradicate threats, ensuring minimal damage and a swift recovery. This phase is critical to maintaining business continuity and protecting sensitive data from cyberattacks.
Selecting SIEM Vendors to Enhance Your Threat Detection Capabilities
SIEM Vendors offer solutions that enable organizations to monitor and analyze security events. With the help of SIEM Vendors, businesses can detect potential threats early and ensure they meet compliance requirements. These vendors provide tools for real-time threat detection, incident response, and security data management.
MDR for MSPs (Managed Detection and Response) allows Managed Service Providers to enhance their security offerings. With MDR for MSPs, providers can offer their clients advanced threat detection and response without needing to build an in-house security team. This service allows MSPs to stay competitive while delivering top-tier security solutions.
In conclusion
The dynamic landscape of cybersecurity demands robust solutions like Network Security Monitoring Services, Managed SOC Services, and MDR Security Services to ensure comprehensive protection. Leveraging the benefits of Cloud Computing Security and integrating advanced tools such as XDR Solutions, SIEM Management Services, and Managed XDR enables organizations to detect, respond to, and mitigate threats effectively.